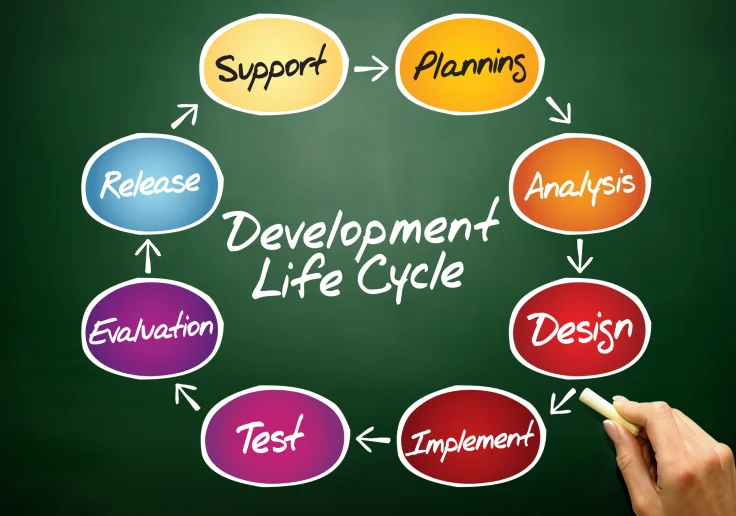
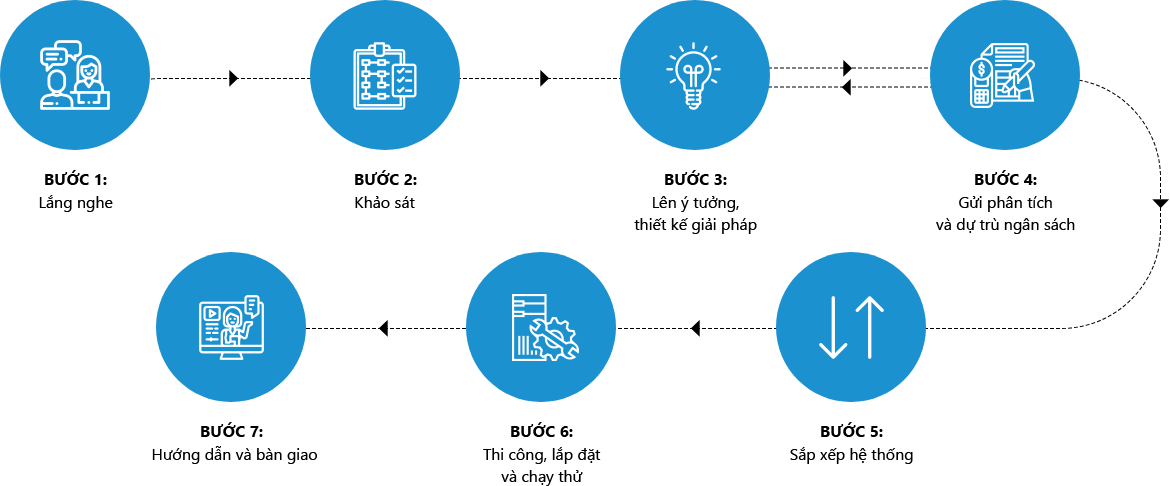
Content
Some tools offer “temporary permission” features, allowing limited time for an employee outside the core team to complete a task. This can make sure business doesn’t slow to a crawl while still offering improved data protection. As a company expands its online footprint, it’s common for several people in the organization to have access to the online tools required to run your business. The principle of least privilege means only the people who really need the tools to do their job should have access to them. For example, your finance team probably doesn’t need access to your code repository, and your development team probably shouldn’t have access to sensitive financial data.
Discovery and onboarding should be automated as much as possible to eliminate shadow IT. Conduct security awareness training for employees, third-party partners and anyone accessing organizational cloud resources. Know what security controls they offer, and review contracts and service-level agreements diligently. Understand the shared responsibility model, including the responsibilities of your CSPs and your security team. Adopt cloud edge security protections, including firewalls, IPSes and antimalware.
Top Network Access Control (NAC) Solutions for 2023
It can be accomplished using a cloud storage service that offers security features such as encryption or access control. CASBs cover a wide range of security services, including data loss prevention, malware detection, and assistance with regulatory compliance. CASBs have integrations with multiple SaaS and IaaS platforms, needing to work with many different cloud-based software solutions to secure an organization’s entire infrastructure. Consider CASB providers that support all your business’s cloud-based tools.
Controls that help prevent issues such as unauthorized access, accidental data leakage, and data theft. They should allow you to apply more precise security controls to your most sensitive and valuable data, such as through native security classifications. Find out more about what cloud security is, the main types of cloud environments you’ll need security for, the importance of cloud security, and its primary benefits. Remember that many of these commonly available cloud storage services don’t encrypt data. If you want to keep your data secure through encryption, you will need to use encryption software to do it yourself before you upload the data. You will then have to give your clients a key, or they won’t be able to read the files.
Protecting your business means protecting your data
Many of the same tools used in on-premises environments should be used in the cloud, although cloud-specific versions of them may exist. These tools and mechanisms include encryption, IAM and single sign-on , data loss prevention , intrusion prevention https://globalcloudteam.com/ and detection systems (IPSes/IDSes) and public key infrastructure . Aside from the security and compliance issues enumerated above, cloud providers and their customers will negotiate terms around liability , intellectual property, and end-of-service .
- A well-designed and business-specific security strategy will help minimize the risks, if not mitigate/ avert all threats.
- Cloud services providers offer logging, and there are third-party tools available also.
- Though the idea of cloud computing isn’t new, associations are increasingly enforcing it because of its flexible scalability, relative trustability, and cost frugality of services.
- These include services such as firewall as a service, cloud-based virtual private networks and key management as a service .
- The lack of clear boundaries poses several cybersecurity challenges and risks.
- As cloud services, including cloud security, are easily scalable, it is a way to support continuity even during times of rapid growth.
- Those updates often contain tools designed to protect your devices from the latest viruses or malware.
A provider that focuses on continuous compliance can protect your company from legal troubles and ensure you’re using the most updated security practices. Work with groups and roles rather than at the individual IAM level to make it easier to update IAM definitions as business requirements change. Grant only the minimal access privileges to assets and APIs that are essential for a group or role to carry out its security companies list tasks. And don’t neglect good IAM hygiene, enforcing strong password policies, permission time-outs, and so on. Was first introduced in 2010 by John Kindervag who, at that time, was a senior Forrester Research analyst. The basic principle of Zero Trust in cloud security is not to automatically trust anyone or anything within or outside of the network—and verify (i.e., authorize, inspect and secure) everything.
Cybersecurity and cloud computing: Risks and benefits
Functional and tested disaster recovery and backup processes need to be in place to counter this risk. Security solutions will need to be built into every network layer to protect against data loss from cyberattacks. But you might have concerns about cloud computing, including data protection, security threats, and potential data loss. You might worry that all those videos, photos, and reports might be vulnerable to data breach and hackers who could break into your cloud provider’s servers. Understanding your security responsibility is the first step to building a cloud security strategy.

Violation of acceptable use policies can lead to the termination of the service. Some key terminology to grasp when discussing penetration testing is the difference between application and network layer testing. Understanding what is asked of you as the tester is sometimes the most important step in the process.
major security threats in cloud infrastructure
Accounts of such users are a goldmine for cyberattackers, as compromising them can make it easier to access critical cloud infrastructure and escalate privileges. It can be challenging to clearly define the boundaries of a company’s cloud environment. Systems and data might be attacked from many angles, including personal devices of remote employees, unauthorized third-party cloud applications and services, and public networks.

Account hijacking or takeover—many people use weak passwords or reuse compromised passwords, which gives cyberattackers easy access to cloud accounts. Business interruption—risk professionals around the globe identified business disruption caused by failure of cloud technology / platforms or supply chains as one of their top five cyber exposure concerns. Using a cloud service doesn’t eliminate the need for strong endpoint security—it intensifies it. After all, in many cases it’s the endpoint that’s connecting directly to the cloud service. Having frequent conversations about topics like data privacy, proper password management, and protecting the physical premises. A complete cloud security architecture addresses the goals by unifying the functional elements.
Access control and strong authentication.
Suppose your cybersecurity specialists notice a user logged in to your cloud infrastructure from an unusual IP address or during non-working hours. In that case, they’ll be able to react to such abnormal activity in a timely manner, as it indicates the possibility of a breach. Describe your employees’ expected cybersecurity habits, including having different and complex passwords for different accounts as well as regular password rotation.